Cybersecurity and Privacy
An Essential Priority within the Mindray Distributed Monitoring Network
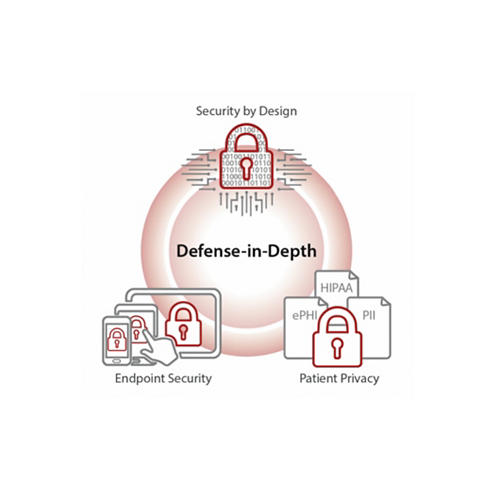
Mindray is committed to protecting patient data and ensuring privacy
The digitization of healthcare in the U.S. continues to accelerate. From Electronic Medical Records (EMRs) to millions of connected medical devices, the flow of patient information is increasing exponentially. With such an increase in the volume and modes of data transmission, there comes a greater vulnerability to cybercrime. As a result, cybersecurity and privacy is an ever-growing concern within the healthcare sector.
Mindray CARE Team Support
When you invest in Mindray solutions,you gain access to the Mindray CARE Team-a serviceorganization dedicated solely to ensuring you get the most use out of your equipment,so youcan ensure your patients get the most out of their care. Our dedicated field service team andin-house technical support organization represent one of the largest direct service teams in the industry.
Purchase from Mindray includes comprehensive clinical training and 24/7 remote technical support.